Overview:
For several years, software architects have discovered and implemented several concepts and best practices to build highly scalable applications. Today, these concepts are even more applicable because of ever-growing datasets, unpredictable traffic patterns, and the demand for faster response times and such growing demands require cloud solution provider to deliver the solutions quickly without compromising the quality.
This white paper is intended primarily for the consultants, architects, and decision maker of ISVs and Enterprises looking for technology partners for implementing cloud computing solutions.
It describes the best practices e-Zest Solutions Ltd has identified in delivering the cloud computing solutions to their customers.
Introduction:
Here are some definitions of cloud computing which are mostly accepted by the industry -
A typical cloud computing stack is shown in the following diagram, where Infrastructure, Platform and Software are offered as services to end users.
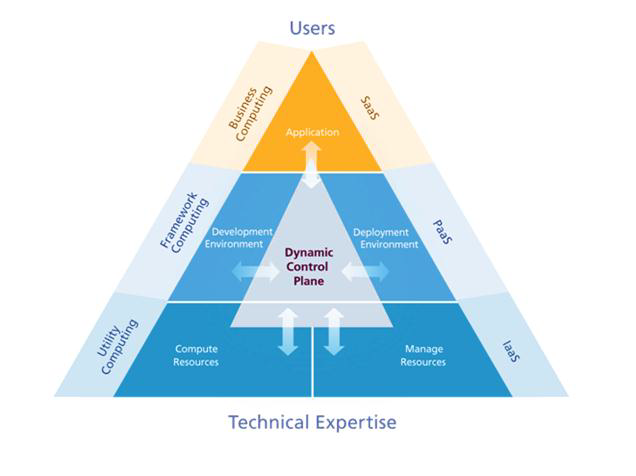 Attributes of Cloud Computing
Attributes of Cloud Computing
The key to understanding the term “Cloud Computing” is to know the typical attributes in a cloud solution. These are off premises computing resources, elasticity, flexible billing, virtualization, service delivery, universal access, simplified management, affordable resources, multi-tenancy, service level management etc.
Best Practices of Cloud Based Solution Delivery adopted by e-Zest:
Solution Delivery at e-Zest starts with assessment phase where benefits and challenges are rigorously studied by our consultants to give customers certain recommendations about ‘moving to cloud’ followed by design, integration, implementation, operation and adaption phases.
This is depicted by the following process diagram.

Assessment Phase:
Cloud Platform Value Assessment includes an impact analysis related to the business strategies, technology and financial implications. This answers most of the questions like why to move to cloud, what to move, when to move, how to move, which platform and service provider to select, what will be the impact on my employees, who will be the sponsor and analysis of investment and ROI.
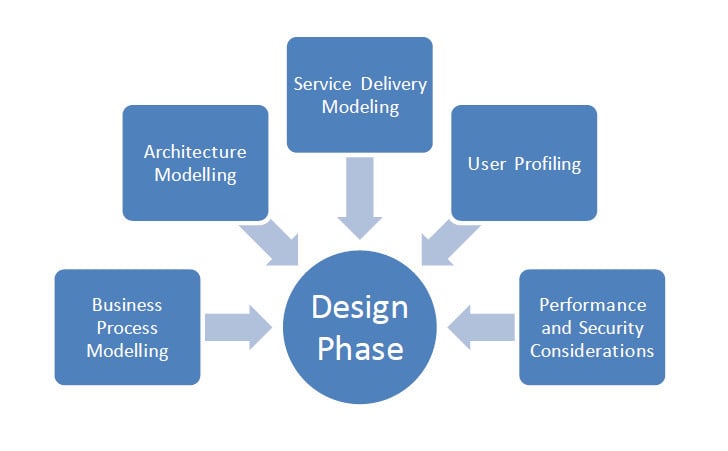
Design Phase:
Assessment phase is followed by Design phase wherein sub-phases like Business Process Modeling, Architecture modeling, Service Delivery Modeling, Multi-Tenancy Design, Configurability and User Profiling are carried out.
Few of these sub phases are explained below:
This is mainly applicable for the enterprises which have complex business processes. The best way to capture the required functionality in business terms is to model these processes and map them to the technologies required to implement them.
This phase is further broken down into business process discovery, business process analysis and business process design.
Before proceeding with the Implementation phase and actually selecting the components it is worth having an architecture blueprint that maps the relevant business processes against the high level technical architecture. Any of relevant architecture frameworks (e.g. TOGAF, Zachman, 4+1 view or even architecture design spikes for agile environment suitability) can be used in this phase.
Certain decisions like whether the application should be built in-house or acquired, which service delivery level to use are formulated in this phase.
There is many-to-many relationship between applications and users with a large no of combinations possible. Identity management, user registration and subscription management, user segmentation like user clustering and partner integration can be performed while profiling the users.
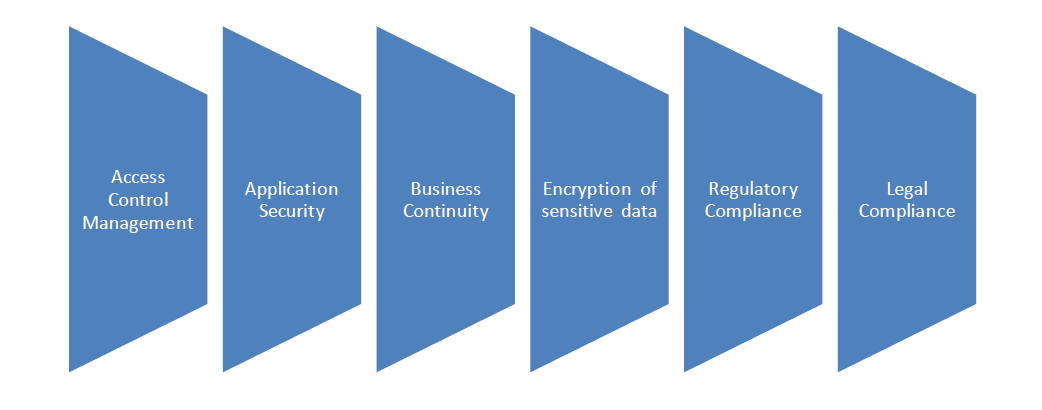
Performance and security considerations
Cloud applications are remote and are accessed by large number of users through internet and mobile devices and hence performance matters a lot. A high response time is expected from the cloud applications. Performance engineering within systems engineering, encompasses the set of roles, skills, activities, practices, tools, and deliverables applied at every phase of the Systems Development Life Cycle which ensures that a solution will be designed, implemented, and operationally supported to meet the non-functional performance requirements defined for the solution.
Access control management: provides mechanisms to protect critical resources from unauthorized access and modification while facilitating access to authorized users. This is implemented at multiple levels e.g. physical access to data center, logical access to end user.
Application security: covers the software development life cycle and principles as well as multi-level security for in house applications.
BCP: includes planning for catastrophic system failures and natural disasters. It also includes comprehensive backup schedules and recovery strategies.
Encryption of sensitive information: Sensitive data in transit and data in rest needs to be encrypted in order to prevent data/information thefts and financial losses.
Regulatory and legal compliances: covers regulations and laws governing information security. Due to multi-jurisdictional nature of cloud computing and the segregation of data owner and data controller, legal questions become much more complex.
Integration Planning Phase
Once you have identified the components you will use in your solution, the next challenge is to determine how to put them all together.
Integration considerations include touch points (different OSs/ browsers/ mobile devices/ Desktops), cloud non-cloud application integration, integration with cloud’s Platform offerings, cloud connectivity and the cloud itself. Also, metering and billing needs to be considered in the integration phase.
Implementation Phase:
Strong project management practices are key to successful implementation of the designed solutions. E-Zest has adapted the following PM framework:
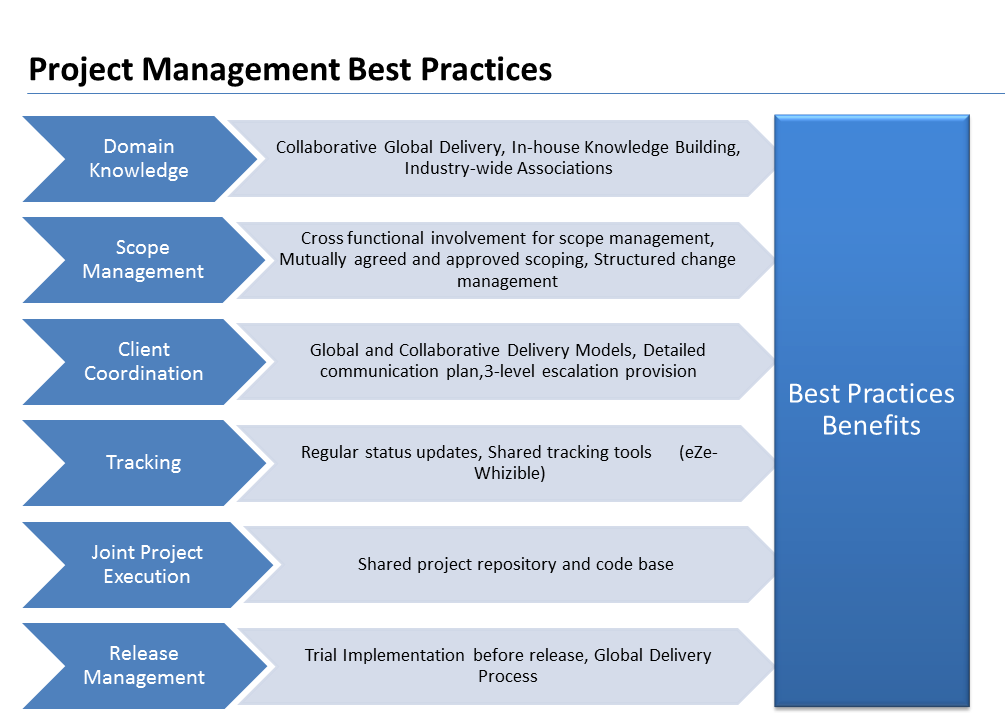
Besides having strong PM framework, e-Zest also has very strong quality management framework and software development process model in place making sure we deliver the highest quality of code faster.
Operate and Control
Ongoing operations management includes data migration, parallel runs, maintenance (preventative maintenances), security monitoring, risk assessment, compliance assessment, periodic security audits, support SLAs and helpdesk systems.
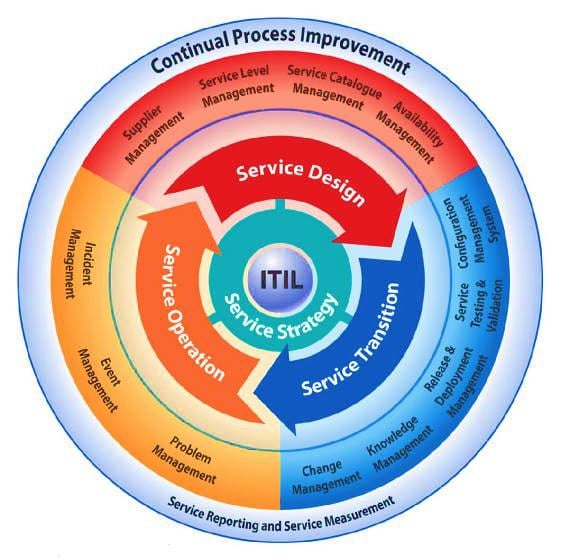
e-Zest follows ITIL service life cycle which implies a service design, service transition and service optimization.
Adapt and Evolve
Cloud computing introduces a new model of IT procurement and planning. Once a service is commissioned, there should not be any need of proactive planning. There should not be any CAPEX in the budget. The provider will automatically take care of all the new upgrades which are in demand. This makes the enterprises “reactive” in approach and poses a danger of not refining their IT needs systematically with the changing business goals over the time. Enterprises need to adapt to the changes quickly by proactively analyzing corporate strategies and making those changes in the acquired cloud solutions.
This calls for a continuous and systematic gap analysis that tracks the execution progress against the business objectives.
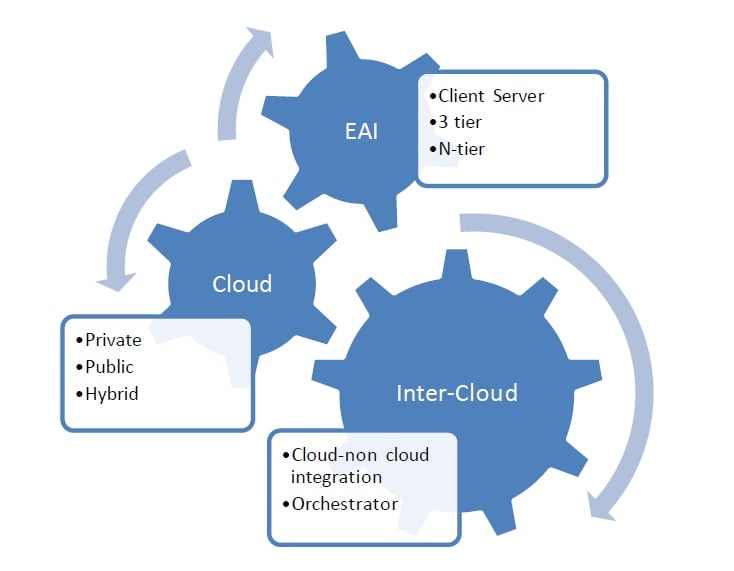
Cloud computing is primarily a virtual phenomenon and fundamentally reliant on networking. Any changes in the connectivity will have a direct impact on the services and QoS.
As a result, the cloud technology providers need to be aware of next generation Networking like persistent connectivity, unified communications and IPV6.
Summary:
Current economic conditions make the “pay-as-you-use” IT service model very attractive to organizations. Cloud computing enables the availability of internet resources and organizations can eliminate the infrastructure costs by moving it’s spending from CAPEX to OPEX.
Cloud computing is complex in terms of implementation and delivery for technology companies. It requires a detailed and rigorous planning during all the stages. Having a good delivery framework in place increase the chances of successful delivery with committed quality and time.
e-Zest has an in-depth understanding of cloud computing based on its strong foundation of SaaS delivery model and experience working with 20+ customers in the domain. eZest has built a strong cloud practice center based on its vast experience on SOA, SaaS and web 2.0. It has strong team of engineers capable of delivering solutions using MS-Azure and RackSpace.
e-Zest is committed to protecting your data. We have designed robust controls to safeguard your data from unauthorized collection, use and disclosure.
e-Zest is a leading digital innovation partner for enterprises and technology companies that utilizes emerging technologies for creating engaging customers experiences. Being a customer-focused and technology-driven company, it always helps clients in crafting holistic business value for their software development efforts. It offers software development and consulting services for cloud computing, enterprise mobility, big data and analytics, user experience and digital commerce.